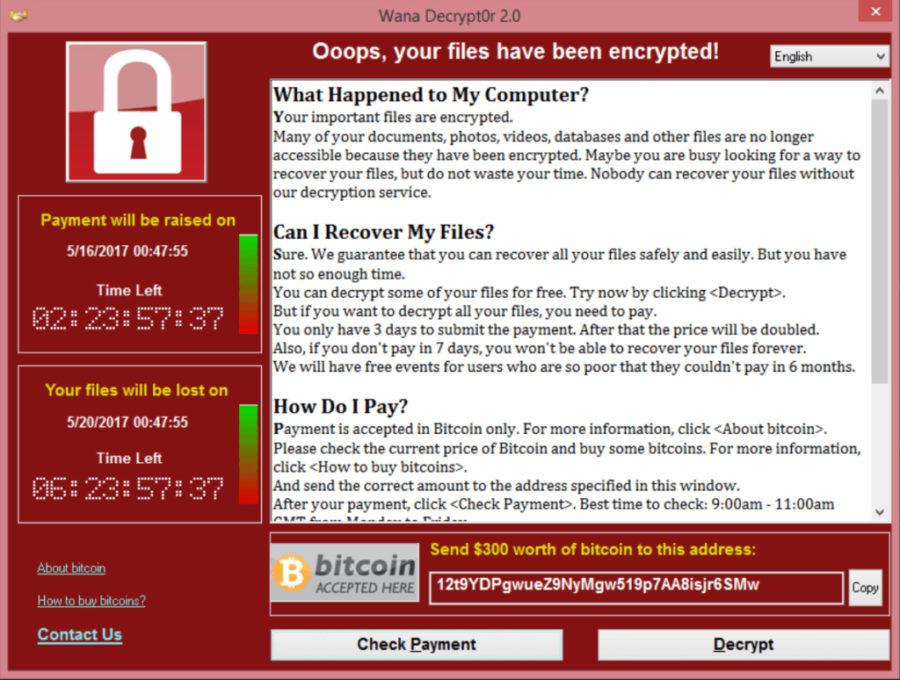
How much is all of the information stored on your computer worth?
A ransomware that spread to more than 100 countries in just a few hours faced thousands with this very question. When infected users opened their computers on Monday, they were met with nothing. All of their files were encrypted by the WannaCry ransomware. If they wanted their files decrypted, the program said all they had to do was pay $300 worth of Bitcoin to the specified address.
But the catch is obvious — WannaCry and its creators have no obligation to decrypt the data if the user pays up. Essentially, people’s entire digital lives have been stolen and are being held for ransom without guarantee.
Ransomware is nothing new. In fact, McAfee, a popular anti-virus software, reported nearly 250,000 new, individual and unique types of ransomware in the first quarter of 2013. These types of infection usually exploit vulnerabilities in networks using Trojan links, seemingly innocuous attachments that deceptively contain a malicious ransomware. When a user clicks on the link, their computer and the information on it is held for ransom while being used to further spread the ransomware.
But WannaCry is unique. When a hacking group called Shadow Brokers released a trove of information containing vulnerabilities and exploits that they stole from the National Security Agency, they opened the internet world to a mass infection of ransomware.
Many parties are at fault here — Shadow Brokers should not have stolen NSA data, and nobody should have created WannaCry. We cannot expect criminal hackers to be held accountable for their actions, but we should hold our government agencies accountable.
Firstly, given its involvement with surveillance and safety, the NSA should have a safer network. There is no reason why our government’s best security experts should not be able to design a network that would prevent this type of theft. But no system is foolproof, and even more importantly, their practice of stockpiling vulnerability is a questionable NSA practice that directly enabled this attack.
Stockpiling vulnerability involves finding and keeping hidden information regarding internet and computer vulnerabilities. The NSA stockpiles vulnerabilities in order be able to effectively combat cyber attacks — if it knows what tools are used in an attack before it even starts, it’s chance of stopping it in its tracks is high.
But WannaCry demonstrates the danger in stockpiling vulnerability — if those vulnerabilities are stolen and released to the general public, anybody with a computer can create ransomware that takes advantage of the vulnerabilities.
Hackers created WannaCry using NSA tools, and it’s not the only malware to be created from government documents. Other reports of cyber attacks developed using information in the Shadow Brokers dump surfaced over the past few weeks. Adylkuzz, discovered at the beginning of May, used the same exploitations and leaks, but was a much larger attack that used infected computers to mine for cryptocurrency rather than demand it from users.
WannaCry rightly scared the general public, but the ransomware shows signs of being produced by amateurs and thus is easily combatted — a 22-year-old discovered a “kill switch” in the program, an easy solution to the growing problem. Adylkuzz, however, is WannaCry’s much quieter, much more dangerous cousin that could have more serious consequences for the world. It is crucial to remember that simply because malware doesn’t reach international news doesn’t mean that it isn’t dangerous, and we should always be on the lookout for malware.
There exists a fine line between fighting fire with fire and simply being careless of the sparks. The NSA’s decision to stockpile vulnerabilities could have already contributed to thwarting other cyberattacks, but there is an easy solution to this problem — if the NSA had alerted Microsoft to the stolen vulnerability, Microsoft could have issued a security patch, as they did shortly after WannaCry spread internationally.
The NSA is on thin ice when it comes to public trust, and if they wish to stay in our good graces they have to prove, with finality, that we can and should trust them to keep us safe.