Cybersecurity remains a tense topic
With celebrities’ naked bodies plastered all over the Internet, deleted Snapchat photos rising from the webosphere and an entire music album mysteriously appearing on your iTunes account, does personal privacy even exist anymore?
Web users aren’t really asking for privacy anymore, according to security expert Benjamin Wittes of The Brookings Institution, a research organization in Washington, D.C. The use or storage of our data doesn’t offend us as long as it’s beneficial, Wittes wrote in a 2011 paper.
We only protest when apps, social media platforms and computer programs like iTunes misuse or fail to protect our data.
“We are, rather, willing participants in our own exposure.” Wittes wrote. “We give away our data at the slightest inducement with full knowledge, at least in general terms, that the companies to whom we give them will use them to market products to us.
The idea behind the popular, more recent photo-sharing app Snapchat is that when you use the app to send a photo, that photo ceases to exist after the receiver views it.
The premise might seem more secure than it is in reality.
Apps like “SnapHack” and “SnapKeep” secretly capture pictures without notifying the sender.
“Given the popularity of Snapchat and the size of our community, it’s no surprise that a cottage industry of app-makers has popped up to provide additional services to Snapchatters,” the company said on its website. “We’ll continue to do our part by improving Snapchat’s security and calling on Apple and Google to take down third-party applications that access our [Application Programming Interface].”
But Snapchat also has most of your information — this time with your consent.
When you first download Snapchat to your smartphone and accept the Terms and Conditions, you actually give the company the right to any information you submit through the app.
Its privacy policy states that the company collects the information users provide through their use.
The policy reads, “For example, we collect information when you create an account, use the Services to send or receive messages, including photos or videos taken via our Services (“Snaps”) and content sent via the chat screen (“Chats”), request customer support or otherwise communicate with us.”
Fadi Alchoufete, a senior computer engineering major at Pitt, said it’s not uncommon for apps to legally mine your data.
“People download an app and it does its job, that’s all you care about.” said Alcoufete. “But, in the background, all that stuff is being sent to their servers. You probably accepted in the terms and conditions that they can take your data.”
Recently, rock band U2 caused controversy by uploading its new album onto all iTunes accounts without users’ explicit consent, which prompted the band to issue a video apology this week.
Sauvik Das, a Ph.D. student at the Human-Computer Interaction Institute at Carnegie Mellon University, said uploading the album without consent was not a security breach because it was a “conscious decision on Apple’s part to promote U2’s newest album.”
Das said Apple can put anything on a user’s iPhone, too. But if a group of attackers compromise Apple’s servers, then they, too, could put anything on a user’s phone.
“So, basically, Apple is sort of the gatekeeper. If you trust Apple’s security, you shouldn’t worry. If you don’t trust Apple’s security, then you can start worrying,” Das said.
According to Das, the recent leak of multiple celebrities’ private photos, such as Jennifer Lawrence’s and Kate Upton’s, was a “security vulnerability.”
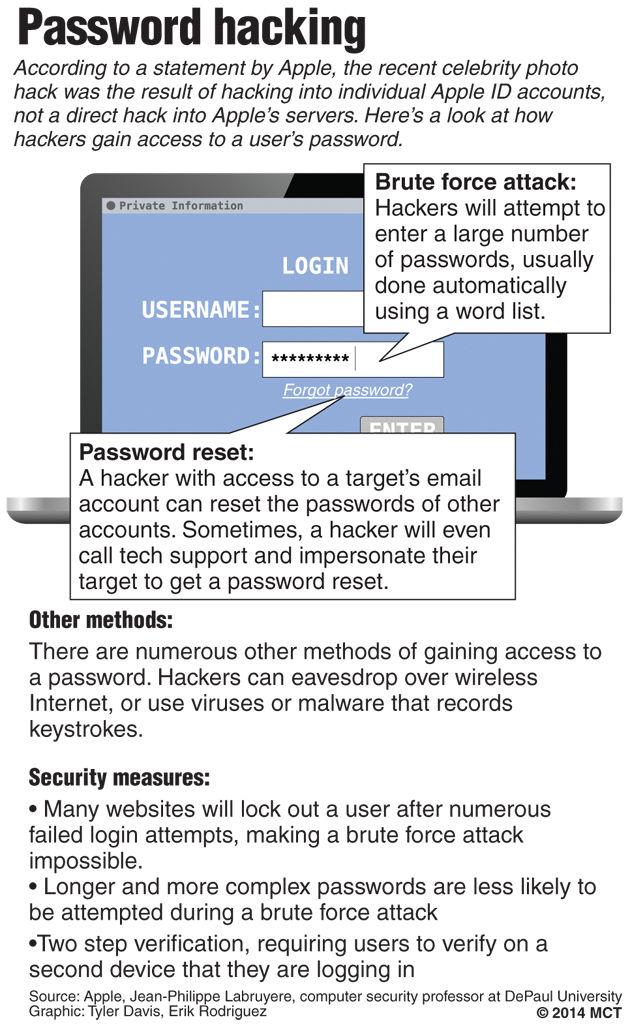
Basically, whenever you create an account on almost any web service, you provide them with a unique identifier (e.g., your username), and then an authentication secret (e.g., your password).
Your identifier is who you claim to be, and your authentication secret is a way for the service to validate that you are who you claim to be.
Typically, if you get you give a web service the wrong password, it lets you try again for a certain number of times before it determines you are not the account holder.
Alchoufete said most security questions have to do with personal history, like “what is your mother’s maiden name?” Given the public nature of a celebrity’s life, this information is not hard to find.
According to Alchoufete, it wouldn’t be too difficult for the hackers to unlock an infinite number of guesses to answer the celebrity security questions and gain access to personal photos.
To protect your online accounts, Alchoufete and Das suggest going beyond the usual security questions and system.
“What I do is I answer the security questions with the wrong answer.” said Alchoufete. “That way, if someone got my information, they still wouldn’t be able to unlock it.”
Das suggests using a two-fold password system, one that requires you to enter a password and then also randomly generates a code, which is sent to your phone. That way, the hacker will have to have both your phone and the correct password.
Das also suggests using a password manager, which generates complex random unique passwords for each account. You only have to remember one strong password for the master account that then takes care of the rest.
The extra step might seem too arduous, but it will result as time well spent.
Wittes writes that privacy concerns become matters of personal security, as privacy breaches can lead to crimes such as identify theft and stalking.
The University does encrypt data, securing it against theft, on its wireless networks, according to spokesperson John Fedele.
Fedele also said in an email that Pitt’s Network Operations Center provides constant technology monitoring and only blocks websites that pose a security risk.
“Should this occur, the site would be blocked on a temporary basis until the threat is resolved,” he said.
Citing as an example, Fedele warned against sites soliciting usernames and passwords in a phishing scam.
To be cautious, Fedele said users should look for a lock symbol in the address bar and ensure that the web address begins with HTTPS (Hypertext Transfer Protocol Secure), indicating the website uses Secure Sockets Layer encryption, a tag that authenticates security, between the device and the website.
“The most important point, however, is to have confidence that you are communicating with a reputable site/organization,” Fedele said.
Recent Posts
Porch roof collapses during party on Semple Street
The roof of a porch on Semple Street collapsed during a St. Patrick’s Day celebration…
A Good Hill to Die On // Break It Down
In this release of “A Good Hill to Die On,” I dive deep into the…
Who Asked? // Does growth only “count” if it’s quantifiable?
This installment of Who Asked? by staff writer Brynn Murawski wonders why it feels like…
“They’re throwing trans people under the bus”: Counseling center faces backlash after event name change
On Feb. 24, Pitt’s Counseling Center faced backlash after briefly renaming an event from "LGBT…
Q&A: Meet the 2024-2025 SGB president and vice president
SGB announced the 2024-2025 election results at their meeting on Tuesday. The Pitt News spoke…
Editorial | Pitt Administration must listen to its students’ electoral demands
The passing of these referendums does not guarantee a future Pitt with these policies. Merely,…